The Decred community considers privacy to be a fundamental human right.
Protecting the privacy of Decred users has been a core tenet of the project since it’s inception. To quote the Decred constitution:
Privacy and security are priorities and shall be balanced with the complexity of their implementations. Additional privacy and security technology shall be implemented on a continuing and incremental basis, both proactively and on-demand in response to attacks.
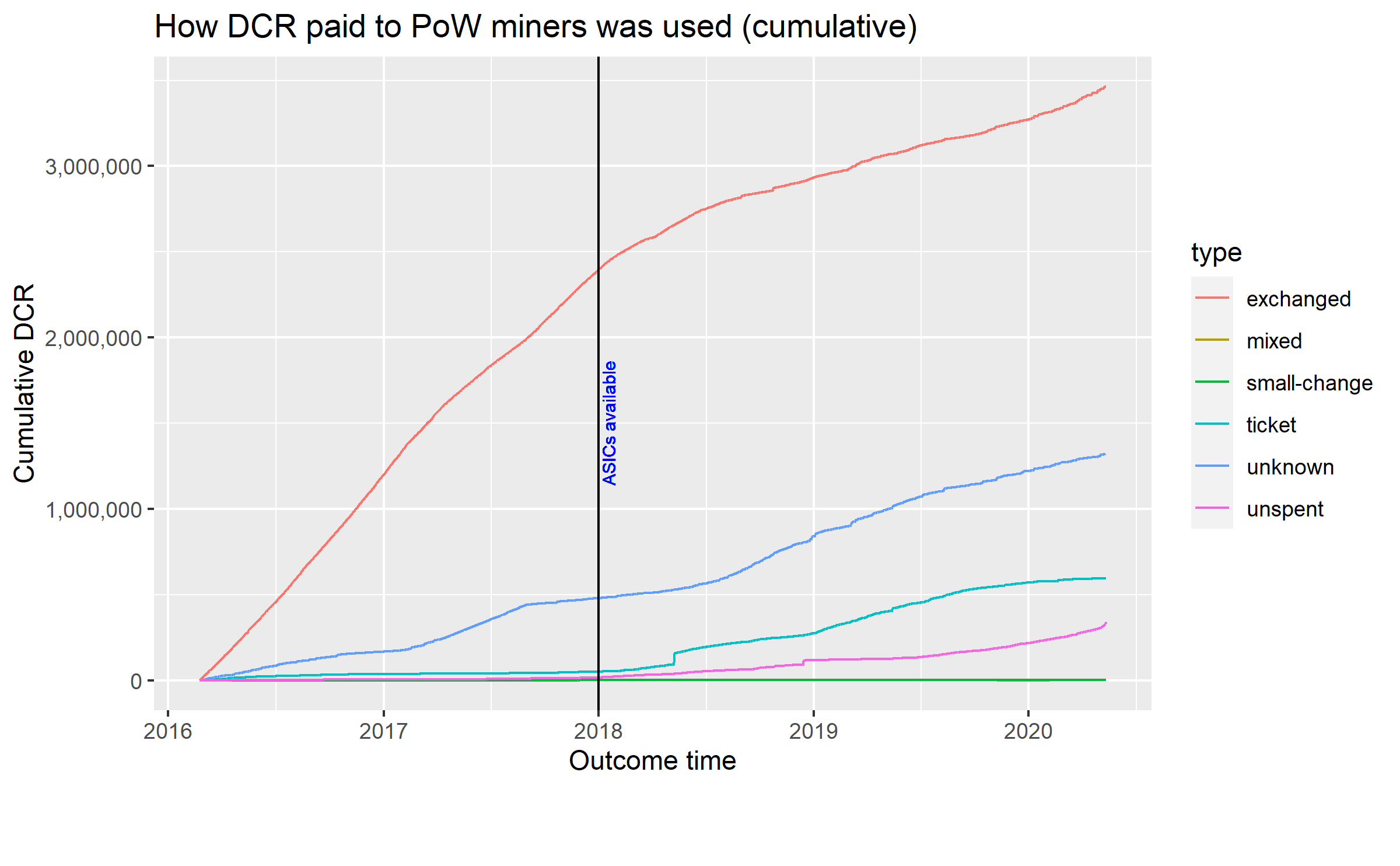
In late 2019, Jake Yocom-Piatt revealed a much anticipated privacy solution for Decred - CoinShuffle++ (CSPP). The introduction of CSPP enables users to anonymize their Decred by mixing with the steady stream of ticket transactions which flow through the network as part of …
Recently Google disclosed a new class of vulnerabilities known as Spectre and Meltdown. Folks in the Decred community have been asking questions about the implications of these bugs for Decred. This post delineates implications of these exploits and possible countermeasures. These bugs are akin to traders issuing cancels without back pressure to manipulate the market.
TL;DR
Run your wallet on physical hardware you control and DON’T share with others and DO NOT run a web browser on the same machine. Hardware wallets do not seem to be affected by these bugs but great care should be taken where they are accessed.